Beyond the Basics—Building a Hacker-Proof Password Reset Workflow
AI
MR Khan
10/26/20253 min read
🔒 Blog: Beyond the Basics—Building a Hacker-Proof Password Reset Workflow
Summary
The common "Forgot Password" workflow is a frequent target for hackers. A basic implementation risks account enumeration, brute-force attacks, and session hijacking. This article details a robust, multi-layered security architecture for password reset, focusing on ambiguous success messaging, cryptographically strong, single-use tokens, strict rate limiting, and proactive security notifications to ensure user accounts remain protected even when a reset is requested.
The Weak Link: Why Your Current Password Reset is a Target
Every application has a "Forgot Password" feature, and because it bypasses the need for the original password, it is the primary vector for account takeover attempts. A basic flow—Enter email, get a link, set a new password—is insufficient. Hackers leverage flaws in this process, specifically:
Account Enumeration: Discovering which email addresses are linked to a user account.
Timing/Oracle Attacks: Inferring system state based on tiny differences in server response time.
Token Brute-Forcing: Guessing or hijacking the secure link.
To counter these threats, we must build a system based on defense in depth.
Foundation 1: Eliminating Account Enumeration
The biggest mistake is confirming whether an email exists on the platform.
🛡️ Strong Measures:
Ambiguous Response Message: When a user submits an email, the success message must be the same whether the email is registered or not:
"If an account matching that email address exists in our system, a password reset link has been sent. Please check your inbox."
Uniform Server Response Time: The back end logic must be structured to execute operations that consume roughly the same CPU time for both registered and unregistered emails. For example, if the email doesn't exist, the system should deliberately wait for a short, consistent duration before returning the message. This defeats timing attacks.
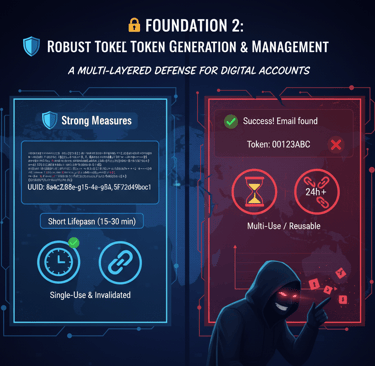
Foundation 2: Robust Token Generation and Management
The password reset token is the most sensitive piece of data in this flow. It grants root access to change the user's password
🛡️ Strong Measures:
Cryptographic Strength: Use a Cryptographically Secure Pseudo-Random Number Generator (CSPRNG) to create the token. It should be a minimum of 128 bits of entropy (a long, non-sequential UUID or similar unique identifier).
Short Lifespan: Set a strict, short Time-to-Live (TTL) for the token, ideally 15 to 30 minutes.
Single-Use and Invalidation:
The token must be immediately invalidated upon successful password submission.
If the user requests another reset link, the previously issued token must be immediately invalidated. Only the newest link should work.
Foundation 3: Strict Rate Limiting
Without rate limiting, an attacker can flood your system with reset requests, trying to guess valid emails or overwhelm your mailing service.
🛡️ Strong Measures:
Limit by Email Address: Restrict the number of reset requests for a single email (e.g., 3 attempts per hour).
Limit by IP Address: Restrict the total number of requests originating from a single IP address (e.g., 5 attempts per hour), protecting against attackers using multiple emails.
System-Wide Limit: Implement a high-level rate limit to protect against resource exhaustion attacks that hit the endpoint with requests from many different IPs.
Foundation 4: Proactive Security Notifications and Cleanup
The process isn't complete until the user's security is fully restored and protected against ongoing threats.
🛡️ Strong Measures:
Request Notification: When a reset is requested, send a separate, immediate security alert to the user:
"A password reset was initiated for your account. If this was not you, click here to secure your account immediately."
Success Notification: Upon successful password change, send a final confirmation detailing the time, and ideally, the device/location of the change.
Mandatory Session Termination: After a successful password reset, the system must log the user out of ALL currently active sessions and devices. This prevents an attacker who may have a compromised session from continuing to access the account after the password has been changed.
HTTPS and HSTS: Ensure the entire workflow—from the initial page to the final submission—is strictly enforced over HTTPS and secured with HTTP Strict Transport Security (HSTS) headers.
By implementing these strong foundations, you move past basic security and build a password reset workflow that is robust against the sophisticated methods of today’s hackers, prioritizing the ultimate security of your users.
Contact
Get in touch with us
Phone
info@tawdir.com
+92 3468828734
© 2025. Tawdir.com All rights reserved.
